Configure EMS Web App to Use LDAP Authentication
Lightweight Directory Access Protocol (LDAP) is an application protocol for querying directory information.
The LDAP Authentication method provides single-sign-on capability using your organization’s LDAP environment. You can use it in intranet and internet deployments of EMS Everyday applications like EMS Web App.
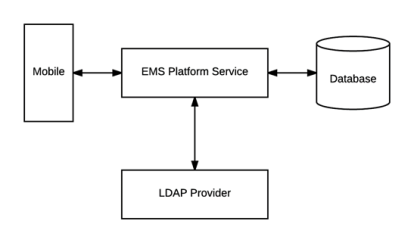
When a user logs into EMS Web App with their user ID and password, their credentials are authenticated against LDAP and compared against corresponding user information recorded in the Network ID and/or External Reference fields of your EMS Everyday User records. If a match exists, the Everyday User is signed in to the application, inheriting any Everyday User Process Template rights to which their LDAP Group has been assigned.
The EMS Web App LDAP-Process Template assignment process requires that your implementation of LDAP stores group information, for example, staff, student, department, and so on as a Directory Service object containing a property, that is member that contains the users that belong to your various groups.
The Field Used to Authenticate Everyday User parameter within System Administration > Settings > Parameters > Everyday User Applications tab is used by the applications to determine the value to be used for authentication.
- Log into EMS Web App with a User that belongs to an Everyday User Security Template containing the Web Administrator role in the EMS Desktop Client under Configuration > Everyday User Applications > Everyday User Security Templates.
- In User Options, select Admin Functions.
- Click the LDAP Configuration tab.
- On the Security tab, select Authenticate users via LDAP to enable LDAP authentication.
- To use LDAP to assign Everyday User Process Templates to Web Users, select Use LDAP to assign Process Templates.
- Enable Use advanced communication options for Active and Non-Active Directory environments.
To enable this checkbox, you must complete the settings on the Communication Options tab.
- In Path for LDAP Query, specify a valid LDAP path, for example, ip:port, LDAP://domain, or LDAP://domain:port.
-
In List of Domains, provide a comma separated list of your domains.
Skip this step if your organization uses a single domain.
- In Network UserId Without Domain Name, enter a directory admin user name, for example, YourDomain\User, LDAP_FullUserId.
- In Password, enter a valid password for the user account entered in the previous step.
- Specify the appropriate LDAP Authentication Type for your environment.
The Communication Options tab includes fields that define how to fetch a Group or a User when sending communications from the EMS Desktop Client. You can also set the SSL configurations, including the Security Certificate Path. Select Use SSL to force communication to use SSL.
Indicate whether your LDAP implementation is Active Directory. These properties are set to the common defaults but can be changed here if the LDAP properties differ from the defaults displayed.
- LDAP Name Property – the property for user name on the user record in LDAP that will be displayed. The display name is default as it is the most common.
- LDAP Phone Property – the property for the phone number on the user record in LDAP that will be displayed. Telephone number is default as it is the most common.
- Domain to append to users – This is unnecessary unless the domain of your user is different from the domain returned from the query.
- Field for LDAP Group Lookup – This identifies the EMS property that must be utilized when performing the search. For example, if you use LDAP solely to assign templates and you want the EMS Web App to look up group membership using a field other than the login name, you must enter that field name here. Currently Assigning Process Templates using LDAP is supported through all Current Auth Methods, that is, SAML 2.0 and Native Auth, and you do not have to use LDAP Authentication to use this.
If your LDAP implementation is not Active Directory, use these fields to redefine the LDAP property names used when searching directory information.
- LDAP Account/User ID Property – the property in your LDAP store that contains the user name.
Example: if sameaccountname=xxxx, then enter sameaccountname
- Full LDAP User ID Format – leave blank unless authentication requires a full path.
Example: cn={0},ou=staff,o=yourdomain
- LDAP Group Category – the property in your LDAP store that contains the group category.
Example: if filter is objectClass=groupOfNames, then property should be groupOfNames
- LDAP Group Name – the property in your LDAP store that contains the group name.
- LDAP Group Member Name – the property in your LDAP store that contains the name of a single member in the group.
Example: if member property is member=jdoe, then property should be member
-
LDAP Group Member User Name Attribute – the property of the user record that corresponds to the group's member property to determine group membership.
This is an attribute unique to the user. For example, if you use the attribute cn for two users – Alice of Copper and Alice of Iron, Alice of Copper is considered a member of the same groups as Alice of Iron.
cn=Alice, ou=Copper, ou=People, dc=Accruent, dc=Fortive
cn=Alice, ou=Iron, ou=People, dc=Accruent, dc=Fortive
These are LDAP query overrides to fetch Groups and Users from the domain. These settings rarely need to override, but can be used to customize queries.
- LDAP query for security groups – query used to search for security groups in your LDAP store. This is required to assign templates in DC.
- LDAP query to find users – query used to search for users in your LDAP store.
- LDAP query for find users with space – query used to search for users that have spaces surrounding their user names in your LDAP store.
- Click Save.
If you want Everyday Users to inherit Everyday User Process Templates based on the LDAP Group(s) with which they belong, see LDAP Groups Tab. Otherwise, you have completed the configuration process.
- Within EMS Desktop Client, go to the Everyday User Process Templates area, that is, Configuration > Web > Everyday User Process Templates.
- Within an Everyday User Process Template, locate the LDAP Groups tab and select the appropriate LDAP Group(s) to map to that Everyday User Process Template.
- Click OK.
- Navigate to EMS Web App > LDAP Configuration > Test Configuration tab.
- Enter your Network UserId Without Domain Name.
- Enter your Password.
- Click Test.
- If your configuration is successful, you receive a message in a green box at the top that includes domain information and the words "Authentication successful" (please see example below).
- If the configuration is unsuccessful, you will receive a prompt stating LDAP could not be accessed. Check your logs to determine the reason for the failure.
